Passwords and Passwords Management
April 2019
Why strong passwords?
It isn’t an individual, or even a room full of individuals who are trying to crack your password.
Rather, banks of computers are being used to perform the task … and computers do not sleep, eat, take smoke breaks, demand worker’s rights, etc.
The top video cards used in PCs to meet the demands of today’s video games cost about $800 and can process data at the rate of more than 14 teraflops (trillion floating-point operations per second).
To put that in perspective, in the year 2000 the world's fastest supercomputer, a cluster of linked machines costing $110 million, operated at slightly more than 7 teraflops.
What makes a password strong?
Password length
Eight characters used to be good enough, but in recent years the minimum suggested password length has extended to at least 14-16 characters.
As cartoon artist XKCD (https://xkcd.com/936/) puts it,
“Through 20 years of effort, we’ve successfully trained everyone to use passwords that are hard for humans to remember, but easy for computers to guess.”
Best Practices
It is better to choose a longer password that is easy to remember than a shorter password that is too complex to remember.
But it still is the case that the password should be complex enough to make it difficult to guess. OK State University Department of Computer Science Page 2 of 8
Instead of a password, we can create a passphrase by appending together several random words, perhaps followed by a number or with special characters separating the words.
The LastPass website (https://www.lastpass.com/) suggests that you, “tell a story unique to you like Fidoate!my2woolsox.”
Passphrase generators
There are a number of websites that will generate passphrases for you.
For example, consider these passphrases generated by the Use a Passphrase website (https://www.useapassphrase.com/), along with the website’s estimates of time to crack them:
tan crew prison mail (13K centuries)
incoming high binding review (33K centuries)
diet extreme flights of (280 centuries)
Password generators
If you prefer passwords, there also are websites that provide you with strong, random passwords.
For example:
The most common passwords of 2018
(https://www.esquire.com/lifestyle/a25570880/top-passwords-2018/)
123456
password
123456789
12345678
12345
111111
1234567
sunshine
qwerty
iloveyou
princess
Admin
welcome
666666
abc123
football
123123
Monkey
654321
!@#$%^&*
charlie
aa123456
donald
password1
qwerty12
Should passwords be changed?
Many experts believe that passwords should be changed on some periodic basis. o In this way, if a hacker cracks a password, they will be locked out again after the password is changed. OK State University Department of Computer Science Page 3 of 8.
Other experts believe that forcing users to change passwords on a regular basis may not help.
Suppose a current password is My!password01.
If this password is cracked and then changed, it might now be My!password02, My!password03, or so forth. (Sound familiar? ☺) This gives the hacker a limited pool of alternate passwords from which to choose.
OSU requires O-Key passwords to be changed every 120 days or more frequently.
OSU also prohibits the reuse of the four most recent passwords.
This is to reduce the likelihood that hackers who have compromised an account simply can try old passwords again in a short period of time.
Same password for multiple sites?
Is it alright to use the same password for multiple sites or accounts?
After all, that makes the password easier to remember.
Best Practices
It is better for each site and account to have its own unique password.
Otherwise, when a hacker has one of your passwords, he or she can get into all of the sites/accounts that share the password.
Keeping track of passwords
If you are going to have a different password for each site/account, you need a way to keep track of them.
Each of these has its strong and weak points:
Sticky notes or a notebook
Text files
Excel files
VeraCrypt and its cousins
Password Managers
A better alternative is to utilize a password manager.
All password managers basically work the same way: they store all of your account IDs and passwords in an encrypted file, controlled by a master password.
One distinction between different password managers is the same one we see with many software products: free vs. commercial.
In general, commercial products will be more full-featured than their free counterparts.
Further, some commercial products charge a yearly subscription fee for all of your devices, while others charge a one-time fee per device.
Another distinction between password managers is this : single vs. multiple computers.
If you manage passwords on only one computer, then just about any password manager will do.
But, if you manage passwords on several computers, then you might want to look at a password manager that stores its information in the cloud. That way, you will have access to your passwords from different computers.
A final distinction between password managers is this: single vs. multiple operating systems.
If you manage passwords on only one operating system (e.g., MS Windows), then you have more products from which to choose.
But, if you manage passwords on several operating systems (MS Windows, Apple macOS, Apple iOS, Android, etc.), then you probably will want to choose a solution that works on all of these operating systems.
According to the DigitalTrends website,https://www.digitaltrends.com/computing/best-password-managers/, here are the top five password managers in 2019:
LastPass (Windows, macOS, Linux, Chrome
Dashlane (Windows, macOS, iOS, Android)
1Pass (Windows, macOS, iOS, Android)
Keeper Security Password Manager (Windows, macOS, Linux)
Sticky Password (Windows, macOS, iOS, Android)
Another product – which is not on this list – is KeePass (https://keepass.info/), an open source, freely-available password manager.
This is the password manager that I use.
KeePass stores your passwords and other information in an encrypted file wherever you want: on your computer or in the cloud.
Its primary target is MS Windows, but it can be run on Apple macOS, Apple iOS, and Android.
Why do I use KeePass?
It is free.
It is not cloud-based, so I have a copy of my file on my computer.
I can check a password or other account information while offline.
It works for me.
LastPass
LastPass is a Web-based solution that stores your files on their servers.
Since it is Web-based, it is available on all operating systems for which you have a browser.
You also can install an extension in Chrome and other browsers to use LastPass more conveniently.
Let’s take a quick look at LastPass.
It comes in both free and premium (pay) versions.
We will be looking at the free version.
After you sign up, you can add items from your account at the LastPass website.
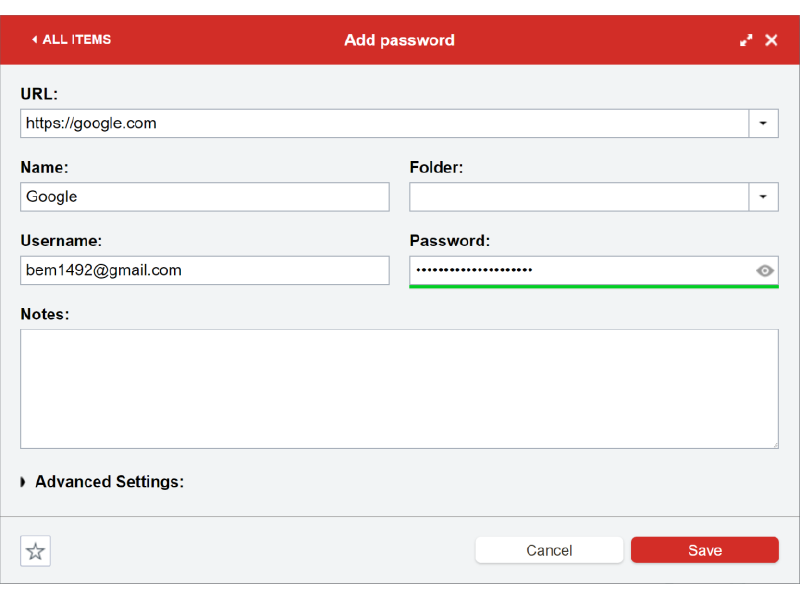
Here, I am adding my google account to LastPass.
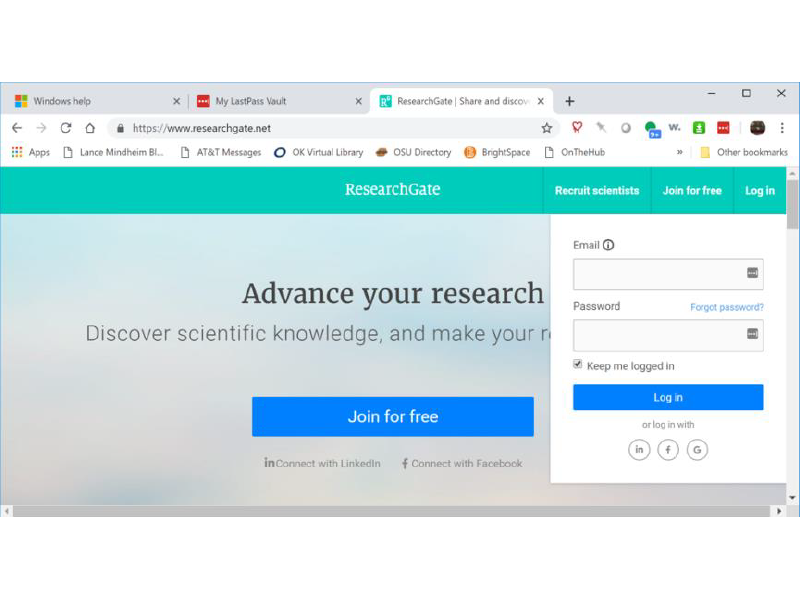
Visiting one of the sites for which I have an account …
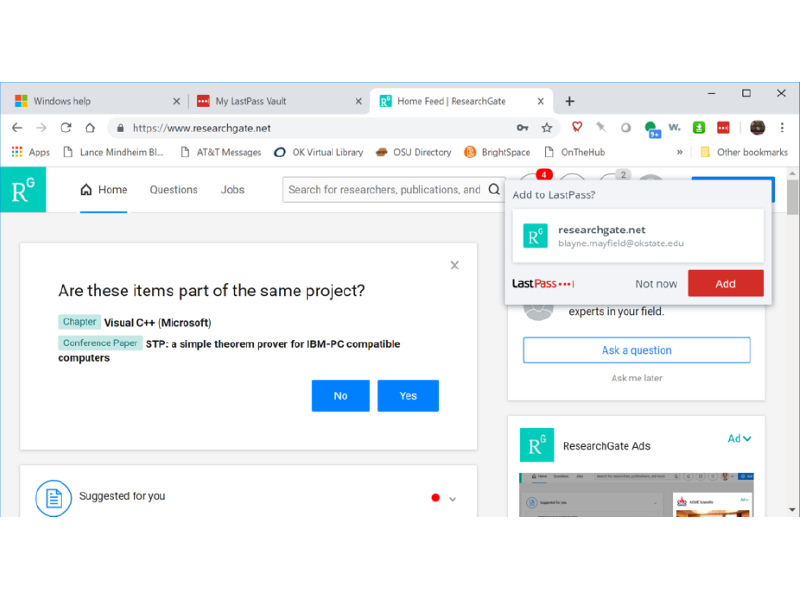
… after entering my credentials, I am asked whether I’d like to add the credentials to LastPass.
The next time I visit, credentials appear automatically.
Best Practices
A few more:
Don’t share a password with others.
If you have your Web browser memorize account names and passwords, make sure that your computer has a good password.
Consider using two-factor authentication.
Two-factor authentication
(https://en.wikipedia.org/wiki/Multi-factor_authentication) Multi-factor authentication (MFA) is an authentication method in which a computer user is granted access only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism:
Knowledge (something the user and only the user knows),
Possession (something the user and only the user has), and
Inherence (something the user and only the user is).
The simplest and most common form of MFA is 2FA, or two-factor authentication.
For example, when you want to sign in to a new Apple device for the first time, you'll need to provide two pieces of information: your password and the six-digit verification code that's automatically displayed on your trusted devices.(https://support.apple.com/en-us/HT204915)
By entering the code, you're verifying that you trust the new device.
So, if you have an iPhone and are signing into your account for the first time on a newly purchased Mac, you'll be prompted to enter your password and the verification code that's automatically displayed on your iPhone.
Another example would be an app or device that requires a password plus a fingerprint or facial scan.
There are a number of products you can use that will require 2FA for your Web-based accounts.
Most use your Apple or Android phone as the 2nd factor for authentication.
This makes it impossible for someone to access your Web-based account remotely, since they do not have your phone.
According to PC World magazine (https://www.pcworld.com/article/
3225913/what-is-two-factorauthentication-and-which-2fa-apps-are-best.
htm) here were the top five 2FA apps for 2018:
Google Authenticator (easiest to use)
LastPass Authenticator (runner up)
Microsoft Authenticator
Authy (best multi-device solution)
Yubico Authenticator
